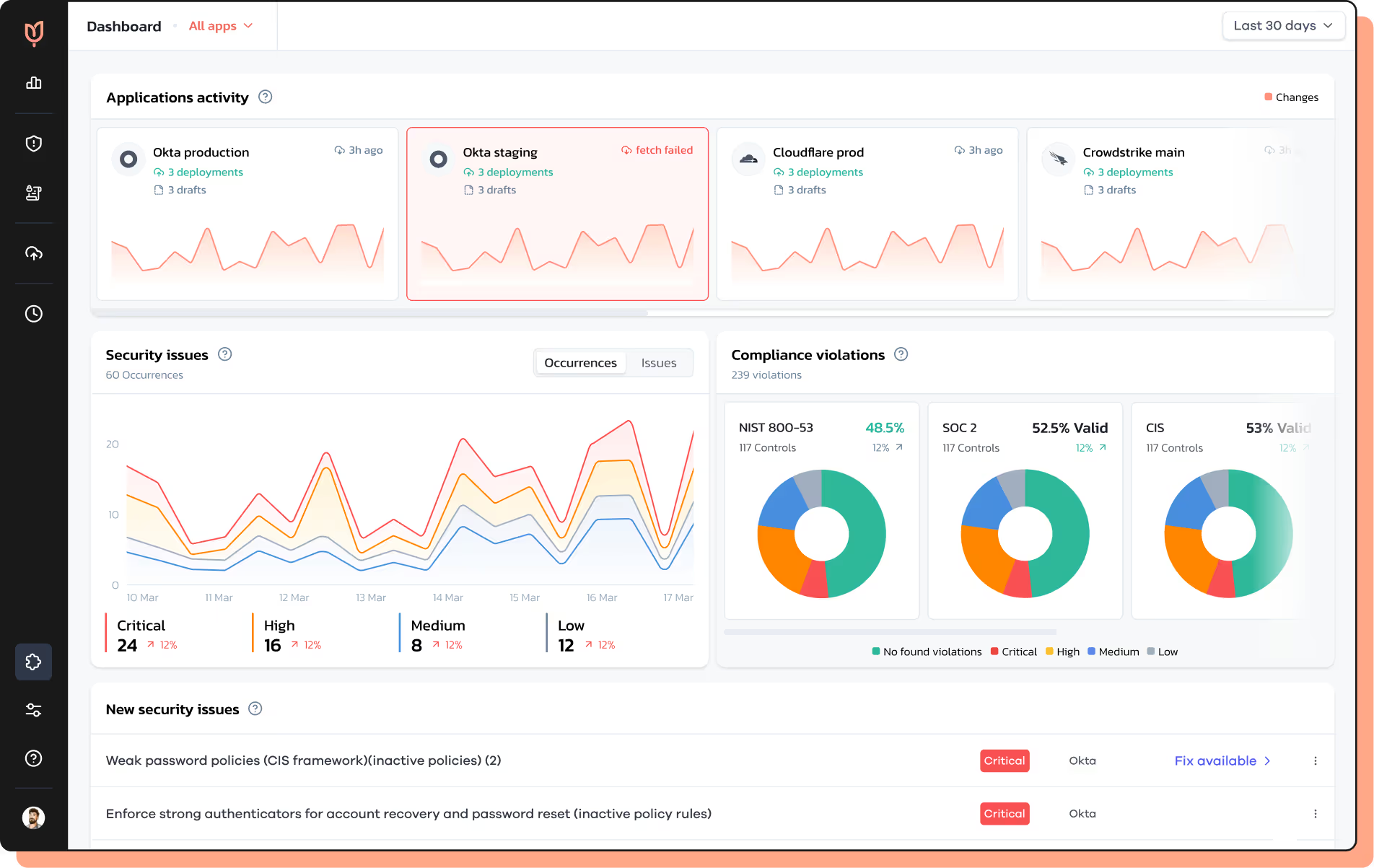
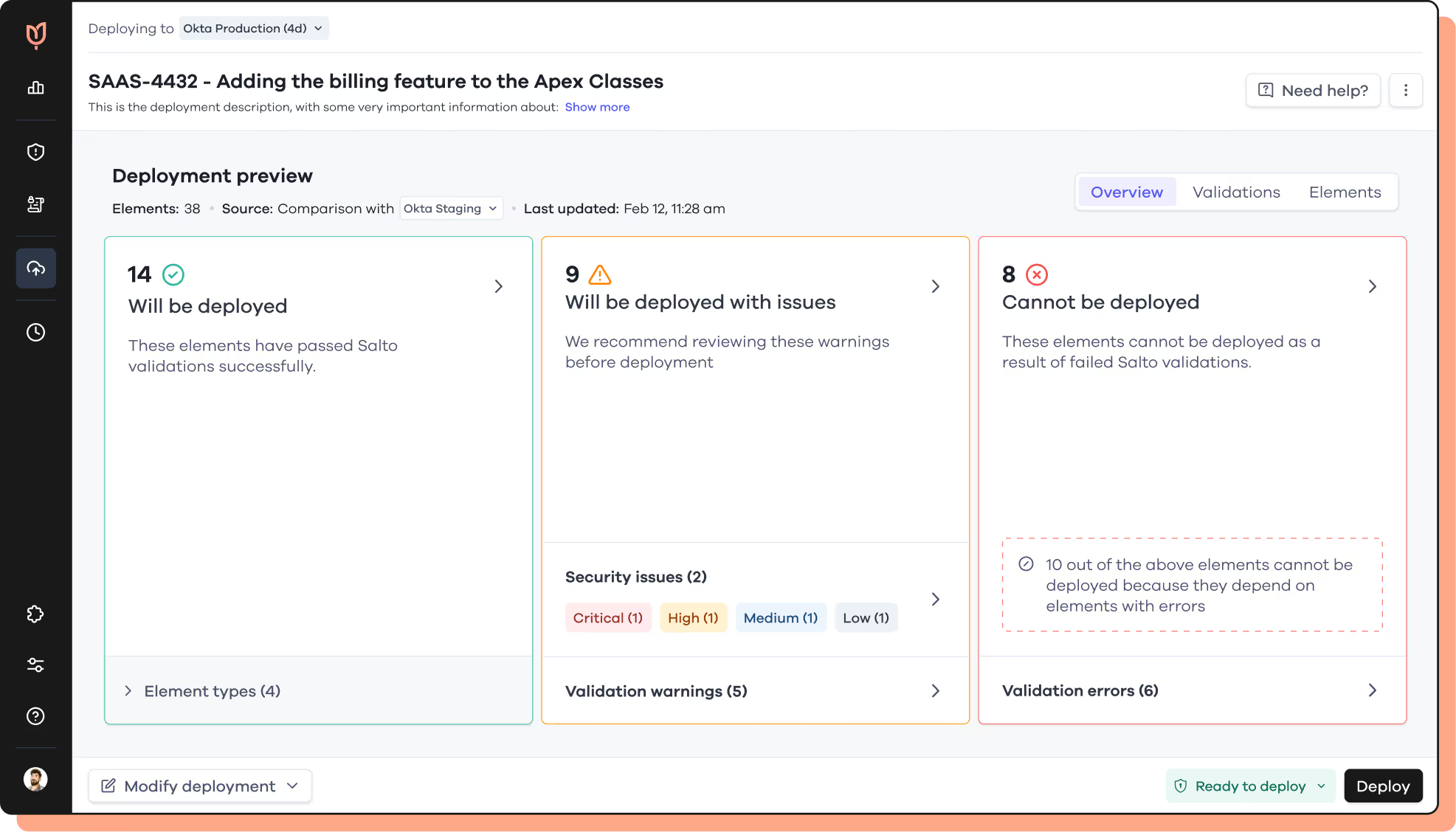
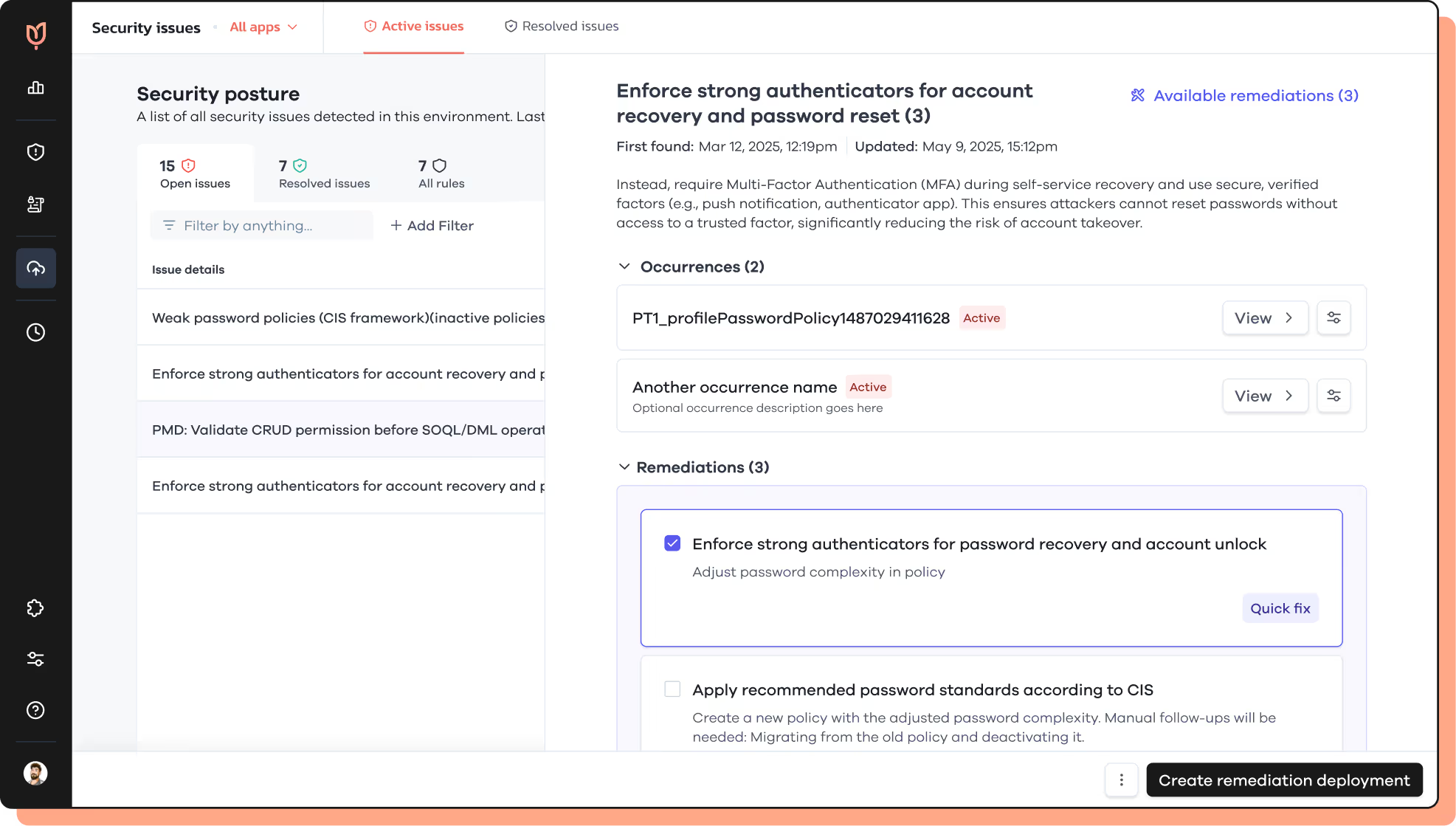
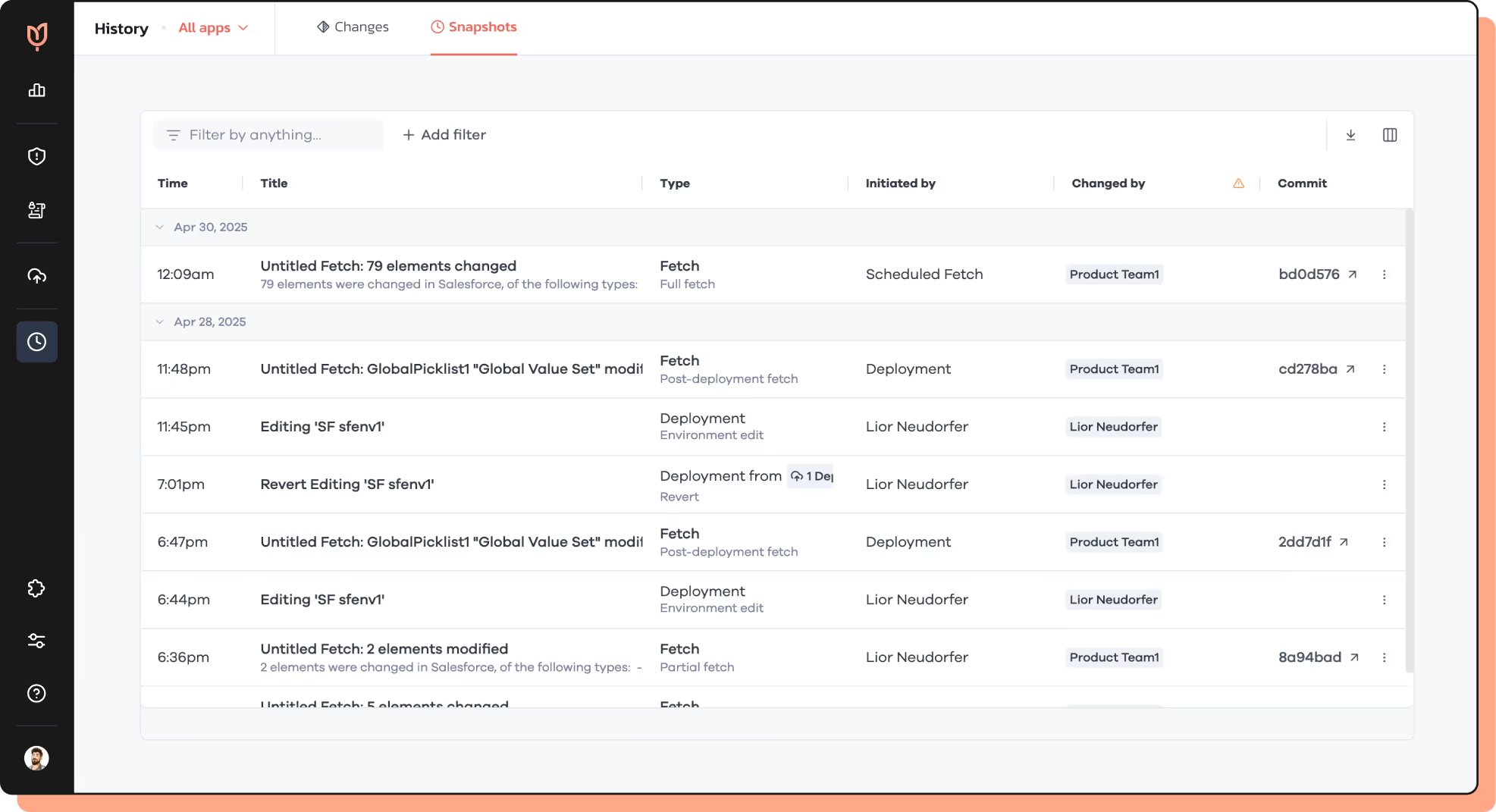
From impact-first planning through continuous detection, automated remediation and drift prevention, Tulip's Security Control Posture Management framework trims misconfiguration risk at all stages, leaving each change audit-ready. Serving as the CISO's co-pilot at the helm of security operations, Tulip orchestrates your workflow, slashing breach windows and audit-prep time, and introduces proper change processes to your controls.



.svg)

.svg)



.svg)






